
SURVEY REPORT: Network Detection and Response (NDR)
With increasingly distributed networks, many organizations are adopting zero trust and cloud-based security strategies (e.g., SASE and SSE) to strengthen their defensive capabilities and reduce their attack surface. This is an important step forward, but a defense-in-depth strategy requires pairing these strategies with advanced threat detection and response capabilities.
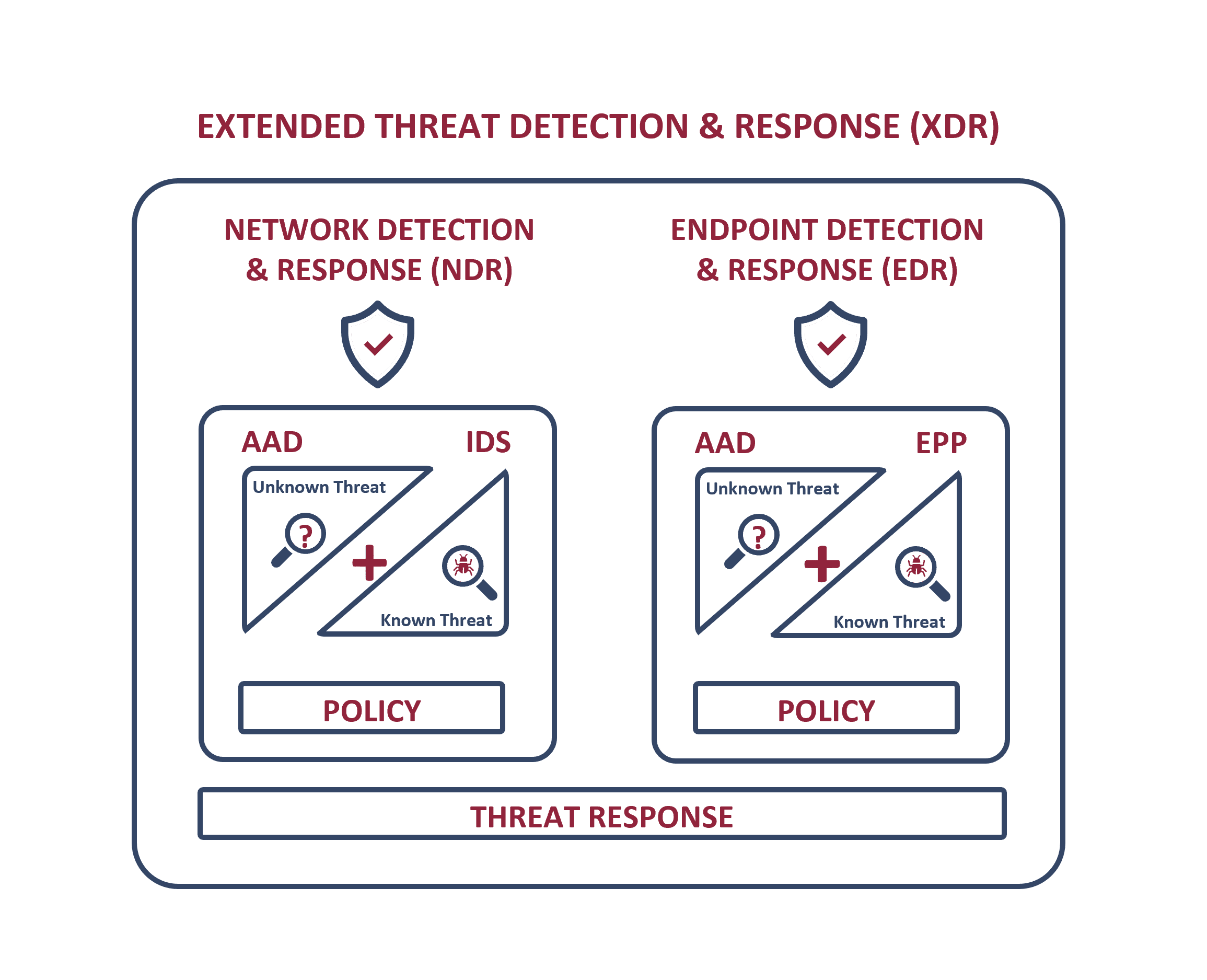
Accordingly, many vendors now offer standalone or integrated Network Detection & Response (NDR) or Endpoint Detection & Response (EDR) solutions, or combine the two in an Extended Threat Detection and Response (XDR) system. These systems use signatures to detect the presence of known attacks, and advanced behavioral analytics (often supported by ML and AI) to detect anomalous patterns indicative of an advanced attack. This behavioral analysis is performed on large volumes of enterprise-wide user, device and network traffic data, with rules for actions to be taken to mitigate potential attacks.
The results of this analysis and the effectiveness of the XDR system depend on the information that is made available to it. The more accurate and precise the data fed to the XDR system, the more reliable and successful the detection of the threats.

As stated, Network Detection & Response (NDR) and Endpoint Detection & Response (EDR) may exist as standalone functions or be combined into an Extended Threat Detection and Response System (XDR). The main role of NDR is to detect and prevent intrusions at the network level, while the goal of EDR is to stop intrusions at the endpoint level (e.g., through anti-virus solutions).
Both NDR and EDR use a combination of trusted technologies: 1. Intrusion Detection/Intrusion Prevention Systems (IDS/IPS) and 2. Endpoint Protection (EPP) to detect primarily known threats, and 3. Machine learning-enhanced behavioral analyses based on Advanced Anomaly Detection (AAD) to identify unknown or hidden threats that have evaded these systems.
Enea’s Qosmos technology not only identifies and classifies network traffic but also provides highly detailed and accurate metadata that provides insights into user and device profiles and actions. It is therefore used as a data foundation to support anomaly detection in both NDR and EDR, and to enhance existing rule-based detection capabilities within IDS and EPP components.
Benefits
“Modern cybersecurity models such as zero-trust networking access and extended detection response pivot around DPI, a trusted technology we all know, but one that’s evolved to meet the needs of the threat landscape today. A strong DPI engine is central to high-performance threat detection. Not only does it enable visibility into network traffic, but it also provides the intelligence around which to base custom rules that customers can tailor to their specific environments.”
Roy Chua, Founder and Principal, AvidThink