WhatsApp-and-dump: Russian-Originated WhatsApp pump and dump attack
WhatsApp’s introduction to the perils of messaging spam took a new twist on Friday the 21th of August, when a large ‘pump and dump’ spam attack was sent to WhatsApp users in the US. We were alerted to this activity on Friday and sure enough large numbers of users on social media reported receiving variants of the following:
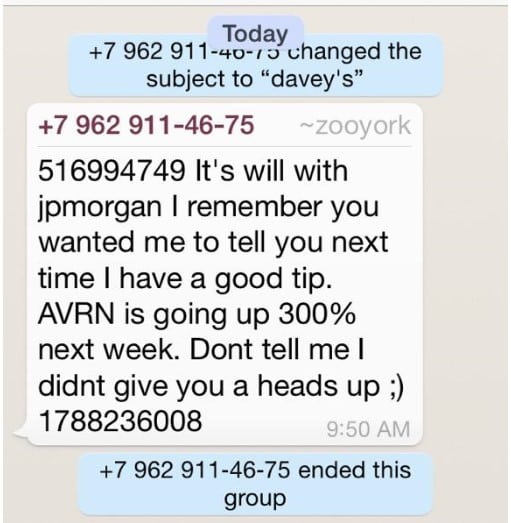
WhatsApp Pump and Dump message promoting the AVRN stock
Pump and What?
Share trading and other sites promptly followed up reporting on the impact of these messages as well on the day. This message – using the latest WhatsApp spammer tactic of adding a user to a group and then removing them – was a ‘pump and dump’ or ‘penny stock’ attack, whose goal is to cause movements in the share price of a penny stock. Featured heavily in the movie the Wolf of Wall Street, penny stocks are a common stock that are normally valued at less than one dollar, and therefore can be highly speculative. The purpose of a pump and dump attack, is as the name of suggests, to pump the stock to be higher using advertising or some form of communications, while the ‘pumpers’ will sell (dump) the stock they acquired before the pump when it gets high enough. These movements – first a large increase while a certain percentage of people may be inclined to buy the stock, and then a large drop as others try to sell off, allow the fraudsters to make money as they typically have acquired shares prior to the pump, and then sell off as it rises.
AVRN itself is the OTCMKTS ticker for Avra Inc, a company that specialises in solutions for the digital currency markets (bitcoin), with several different areas of focus. However according to their latest 10-Q filing at the OTC – they are a company whose financials are exceptionally weak, who have never made any revenue and with total assets of just over $26k. There is also a question on their actual physical location. Their registered location in their 10-Q also seems to be the same Palo Alto, California, address as a Notary Public store called Greemail, while the company HQ address on their website seems to be the same Greenville, South Carolina address as a Advanced Merchant Services branch.


1) Store at 10-Q Registered Address of Avra Inc & 2) Store at Company Website Address of Avra Inc
Previous reports had called out Avra as being promoted heavily in the past, with warnings not to buy. Unfortunately in this particular attempt the pump looks to have been very successful. At one stage on Share prices for AVRN increased by over 640% on the 24th, from their opening price of $0.17 to their height of $1.26, before swiftly dropping off to a close of $0.19. Volume traded during the day was also huge, up to 5,136,600 trades, far in excess of the average of the ~14k per day for the previous 3 months.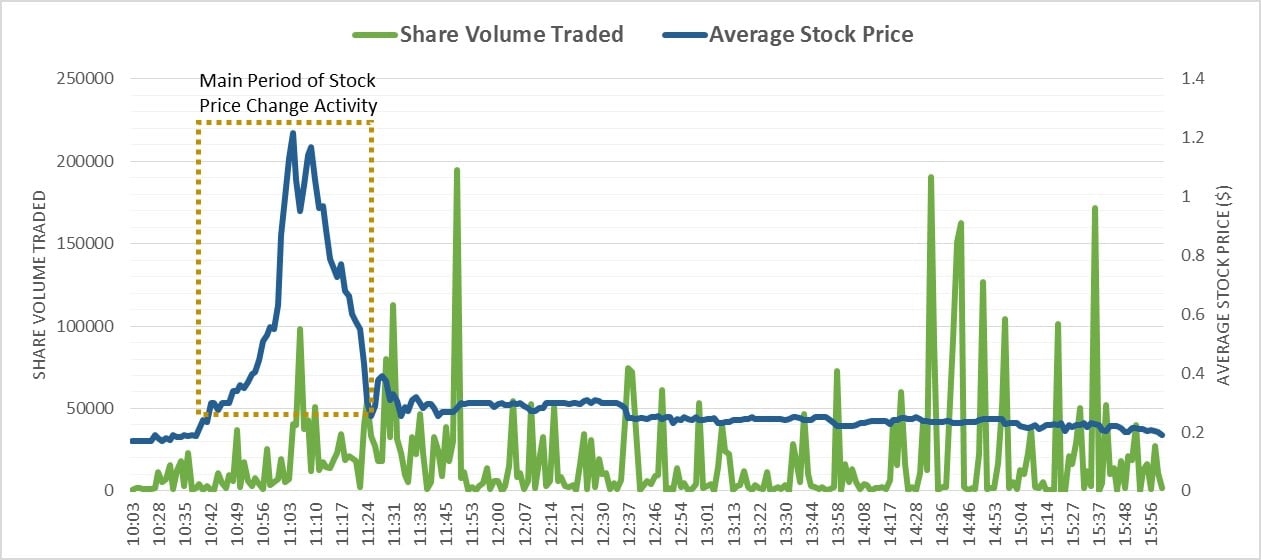
AVRN Stock & Volume changes on 21st August
In fact, if we break down the share trading activity for that day, we can see definite signs of when the pump and the dump occur. The OTC – the market on which this stock trades – opens at 9.30am EST, but no activity occurs until 10:03 when some small trading begins. The stock rapidly increases in the morning, reaching a peak around 11:03. Around this period there is some trading that causes a slight drop, and then finally crashing. It is supposed that in this period the fraudsters dump their stock, gaining the maximum value. Everything after this point are trades which cause little change in aggregate to the stock price, even though the volume is much larger. This activity in the later stage of the day is more likely to be those who received the message either buying or selling the stock, and market speculators attempting to trade on the volatility which has essentially ceased. Altogether, the total value that changed hand in this one day (volume x average share price for that minute) was $1.713 million dollars, with the period of the large price increase & decrease (from 10:40 to 11:25) accounting for $636k, and the spike alone on the 11:03 responsible for around $93k. In can be considered that this is probably a good initial ball-park figure for the amount received by the fraudsters, if they were responsible for this trade. No doubt the SEC will investigate all of these trades, and any suspicious activity prior to this in some more detail.
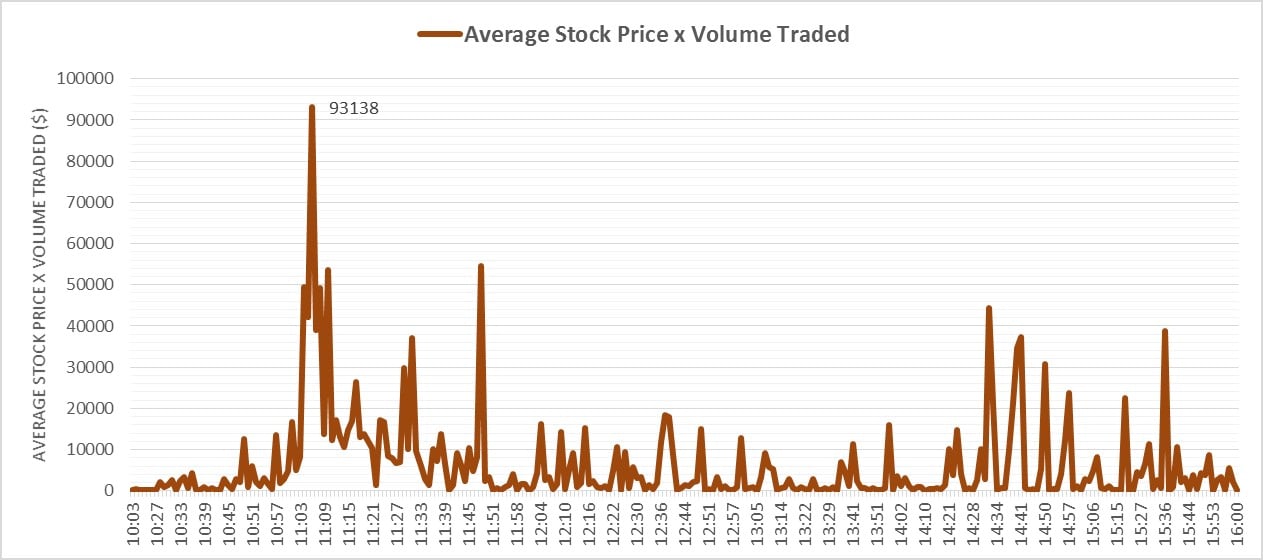
AVRN Value Traded on Friday 21st
A Friend in Russia with Stock Advice
While interesting financially, of more interest to us, is how the attack was conducted. The attack seems to have been begun with messages being sent in the early hours/morning of Friday the 21st , to US WhatsApp users. As covered it used the tactic of adding a user to a group and sending him the message, before removing him from the group, while the name of the group itself is modified. Previously we have covered Whatsapp spam originating from China, India and US OTT numbers. This attack was different in that it originated from Russian mobile numbers (+79). WhatsApp spam from Russian sources have not been a major feature up to now, other than some adult type spam messages, so it seems likely for this attack that the fraudsters decided to work with the same Russian WhatsApp spam sending group or a group very like it, as the same method of adding a number at the start and end of the message is identical- here highlighted with a red box.
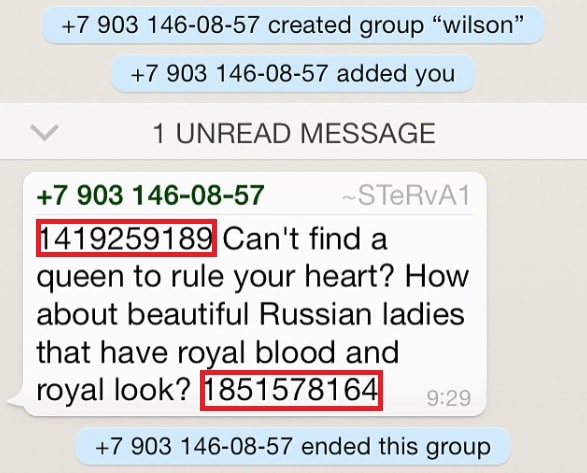
Previous WhatsApp spam reported from Russia
The social engineering in the message itself was relatively simple but interesting:
- It’s will with jpmorgan I remember you wanted to tell you next time i have a good tip. AVRN is going up 300% next week. dont tell me i didnt give you a heads up
- hey it’s tom at jp morgan I want you to know that AVRN is posed to at least quadruple next week. If there is one stock you want to buy it’s this one. Send me a text and thank me later
- yo its gary at citigroup you gotta do me a favour and buy shares at AVRN now. That thing is to at least triple fast. Something huge is about to happen.
- How goes it its ethan with deutschebank I am just letting you know that AVRN is getting a buyout at any moment now. The shares are gonna be trading for 5 to 10 times higher at least. Buy it now. Make some profits and I expect u to take me to the best dinner in town next week on you 😉
- Hey this is jack from morgan stanley. I just got a tip about the stock AVRN… Its gonna double in the next few days. Just wanted to give u a heads up
- watsup patrick it’s john at morganstanley you wanted to know next time I had an “inside”? Dont tell anyone but AVRN is getting a buy out next week at $1 a share. If u wanna buy do it now.
- Hi its ed at goldmansachs I hope the familys good. Listen my “guy” just sent me a msg saying that AVRN is going to a dollar so if u wanna make a move and buyit shud do it now. Txt me later let me know how it goes.
- Howdy its kelly wit jefferies I want u to go take a look at AVRN – this stock is going off the chain we all agree here at the office. Its’s receiving a buyout offer next week and it should be at 2bucks a share. Txt me after u make ur profit and I might have another good one for u in like two weeks
- Hey it’s jose at goldman just letting you know that AVRN is a good buy if you wanna buy it now. My guy told me it’s gonna at least go up 2x by tomorrow
There seem to have been many variants of the message, all revolving around a ‘friend’ in a financial institution advising them they should purchase stock in AVRN, as it is going to increase. One unusual feature was that there was no call to action i.e. a phone number or url in the message. This means that the fraudsters rely on the receiver being interested enough to actively search out the stock itself – reducing their ‘conversion rate’ – but then making the message seem more plausible from this ‘friend’. Overall these tactics seems to have had the desired effect.
We’ve Been Here Before
There is also a question of how many people received this message. Well in this case, there is data from other messaging pump and dump attacks that we can turn to help us guess. Pump and dump attacks over other forms of messaging do happen, but are not common for a few reasons – not least in that they tend to draw a lot of attention and are cracked down on very quickly. A recent, relevant attack though was a pump and dump attack over SMS that was facilitated by the Bazuc message-sharing app. This malware, which allowed users to rent out their messaging plan, was the host of a pump and dump sms message for a particular penny stock sent from Bazuc-hosting cellphones in the US in September/October 2013:
Buy Signal Alert – [REDACTED] – [REDACTED] is hot. Get in now and look for potential 3000% gain. [url=http://www.hot-stocks.com/]http://www.hot-stocks.com/[/url][REDACTED]
We covered this in depth in a previous blog in the past , and in various industry presentations complete with the obligatory Wolf of Wall Street references, but the overall effect was sizable & serious. Within our US carrier customers we detected and blocked messages sent to nearly 100k US mobile numbers. Assuming that roughly the same number of messages were received by other US mobile users (due to activity in other carriers for example) then we can look at whether unblocked spam sent for this stock affected the volumes traded. As messages that are blocked in the carrier network don’t influence a mobile user, then another way to do this is show complaints submitted by mobile users for receiving this spam message (right axis) against volume traded (left axis). This does indicate a loose correlation, at the least signifing that spam activity causes trade increases
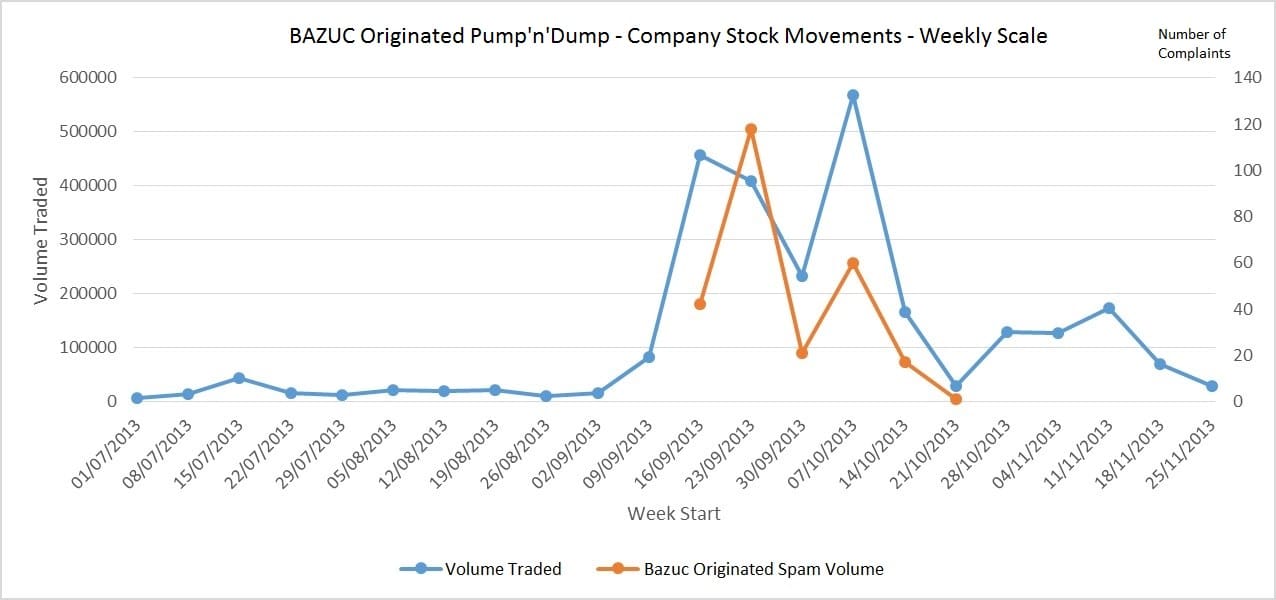
Pumped Penny Stock Trading Volumes v Number of Penny Stock Spam Complaints
In this particular case, over 2 million trades for this stock were made on this stock in the month of September/October – much lower that the AVRN case of 5 million in one day – so we could safely assume that AVRNs 5 million+ trades must have meant that high tens of thousands/ low hundreds of thousands of WhatsApp users received this message.
Old Scams, New Stock & Technology, Same Old Result?
Ultimately, as we predicted at the start of the year, WhatsApp is going to receive more and more of these type of attacks. They have already taken some action by allowing users to report spam that they received within groups, but this seemingly did not prevent this attack occurring, and with the money earned by these fraudsters, there is every reason to assume that they will try again. In fact it will be interesting to see if there is another pump-and-dump attacks in the next few weeks, as some of the ‘friends’ in the various messages reported. While various commentators on social media say that they will move from WhatsApp to other messaging apps, this ignores the point that the same thing may eventually arise there. These attack types are not new, only the medium on which they are being sent, therefore all messaging app companies should try to prepare in advance for these type of attacks, and use the expertise and experiences of the wider messaging security industry.
Update: 25-8-15. Added some additional information on Avra Inc in 3rd paragraph of blog






