Get Ready for Post-Quantum Cryptography with Enea Qosmos Technology, Part 2 of 2
Boost the Performance of Your Post-Quantum Cryptography (PQC) Migration Solution
As shared in Part 1 of this blog post, integrating Deep Packet Inspection (DPI) and new threat detection software technologies into PQC migration solutions can make them more efficient and effective, whether those solutions are provided by software vendors, managed security service providers or internal IT teams. Designed for embedded use in 3rd party applications, Enea’s OEM deep packet inspection (DPI) product, the Enea Qosmos ixEngine®, and Enea’s intrusion detection software development kit, the Enea Threat Detection SDK (TD SDK), deliver unique visibility into all aspects of a network, including applications, services, devices, users, and traffic behavior.
These insights have long enabled optimization and innovation in a broad range of networking and cybersecurity products, which today includes specialized PQC migration platforms as well as PQC migration functions integrated into other types of other solutions, including:
- Network and/or Security Monitoring solutions.
- Host- or Network-based Intrusion Detection Systems (HIDS, NIDS).
- Network-, Endpoint- and Extended [Network + Endpoint] Threat Detection & Response platforms (NDR, EDR and XDR).
- Security Information & Event Management systems (SIEM).
DPI and IDS are particularly valuable in PQC migration because the deep visibility they deliver is valuable to all phases of PQC migration, but especially the pivotal first phase: discovery. To recall from Part 1, there are four general phases of a PQC migration:
- Discovery: identifying all cryptographic resources present on a network.
- Planning: determining which of those resources needs to be upgraded or replaced, and crafting an action plan to do so.
- Execution: implementing the action plan.
- Monitoring: engaging in ongoing network monitoring to detect any signs of migration-related functional or performance issues.
The first phase, discovery, is often cited as the most challenging part of PQC migration. This is because the phase entails developing a complete inventory of all cryptographic elements in a network—including keys, certificates, algorithms and algorithmic libraries. But as these cryptographic elements are entwined in every facet of contemporary networks, the true foundational task of the discovery phase is to achieve 100% visibility across the entire depth and breadth of a network – or to get as close to 100% as one can. If that sounds daunting, it is because it is! But Enea DPI and IDS components can make the task much easier.

Overcoming Discovery Challenges with DPI & IDS
First, with regard to global visibility, one reason it is hard is because most data-gathering tools extract information from only a narrow slice of all assets and activities. For instance, endpoint management systems can provide a granular look at crypto ciphers and protocols in use, but they can only do so for the devices they manage with installed agents. And the percentage of unmanaged devices on networks remains persistently high, as Arista Security expert Rudolph Araujo observes:
“I think customers are expecting network solutions to actually give them an effective map of their network because they realize that the endpoint solutions are just blind to 30, 40, 50% of what’s on the network. Our own data show that [the figure is] somewhere between 50 to 60%.”
Rudolph Araujo, VP, AI and Security Products, Marketing and Strategy, Arista Security
(2024 State of Threat Detection Webinar Excerpt – The Value of DPI-Based NDR Sensors for Attack Surface Discovery)
DPI on the other hand, can extract device-related metadata from network traffic that provides insights into both unmanaged and managed devices, including the way those devices interact with other network elements within a broad range of cryptographically-relevant contexts. This includes who or what is using a device and how they are using it; how, where and when data is being accessed; and how data is moving within and across networks. This kind of deep contextual information is ideal for revealing behavioral anomalies that need to be addressed to produce a complete PQC inventory. As Custocy CTO William Ritchie states:
“The amount of surprises we get during [DPI-powered] mapping is great just for selling our NDR product because customers know that it’s actually working and we have a good visibility on the network. We say, “Well, you’ve said you have 2,000 IPs, you have 5,000. You’ve got a virtual network that you’re unaware of. You have something that keeps pinging your network. Are you aware of this server?”…Not only do we map out the different assets, but we also characterize them and we say, well, we find that this is acting like a server, or whatever, and we validate that with the client.”
William Ritchie, CTO, Custocy
(2024 State of Threat Detection Webinar Excerpt – The Value of DPI-Based NDR Sensors for Attack Surface Discovery)
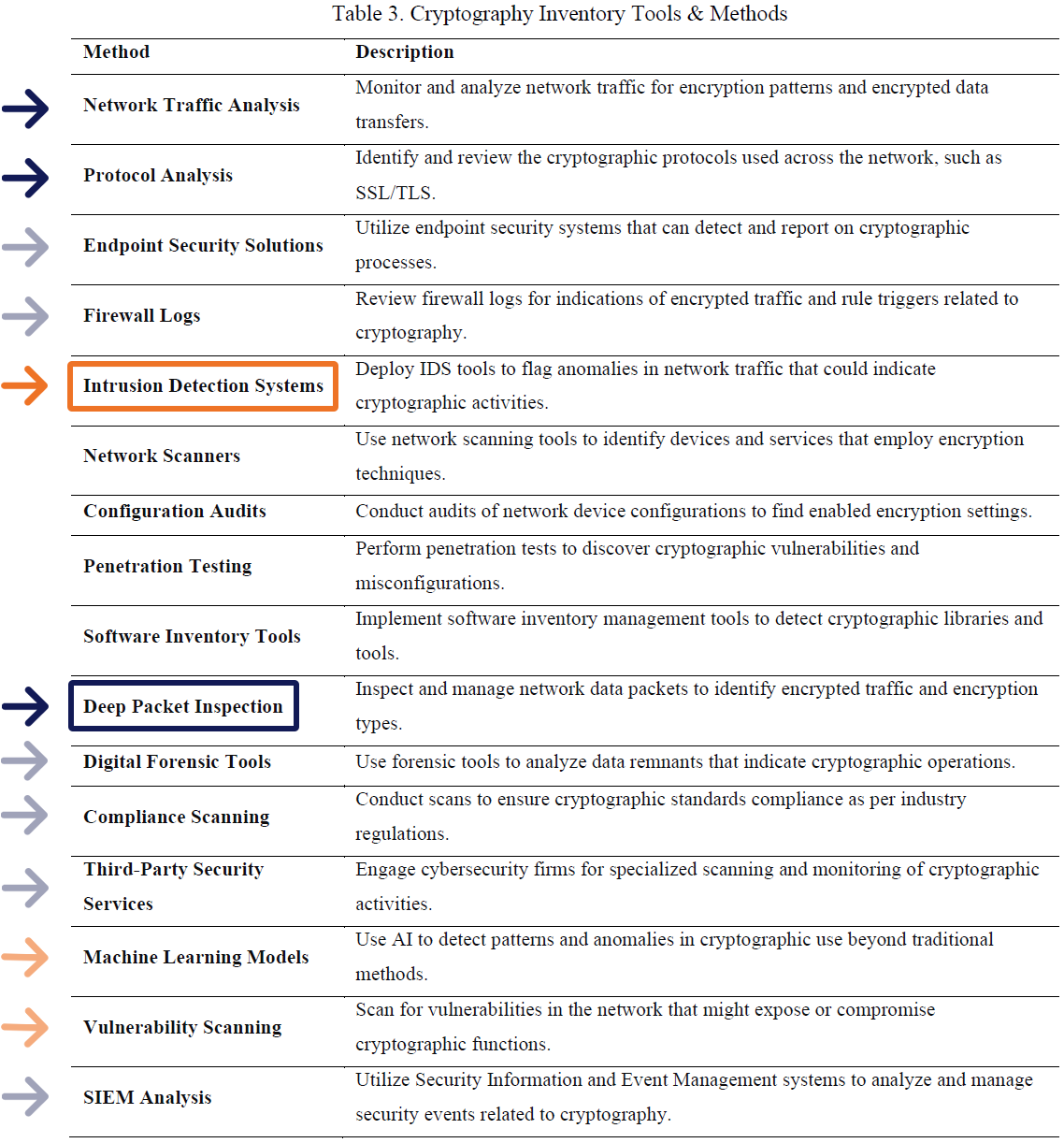
Such blind spots are a major reason DPI and IDS are frequently recommended as tools for facilitating PQC migration, as in the table below from the research paper “Preparing Critical Infrastructure for Post-Quantum Cryptography: Strategies for Transitioning Ahead of Cryptanalytically Relevant Quantum Computing.”1 As indicated by the colored arrows added here, DPI and IDS are not only present as primary tools in the PQC inventory toolbox, they are either embedded or provide complementary functionality or data to most other PQC discovery tools.
DPI Core Function DPI as an Embedded or Enabling Function
IDS Core Function IDS as an Embedded or Enabling Function
The Unique Contribution of Enea Technology
The Enea Qosmos technology is available as a software development kit (C libraries) – the Enea Qosmos ixEngine – or a standalone sensor (Linux application) – the Enea Qosmos Probe. They are developed specifically for integration into commercial-grade 3rd party applications. They identify 4600+ protocols across enterprise, cloud/SaaS, M2M (ICS/SCADA), IoT and AI domains, and extract 5900+ types of metadata, including extensive security-related metadata.
The Enea Qosmos Threat Detection SDK (TD SDK) delivers IDS-based threat detection as a software component. It embeds core functionalities from the open source IDS, Suricata, in a software development kit (SDK) that integrates tightly with Qosmos ixEngine, thereby eliminating double packet processing, accelerating parsing speed, and vastly expanding the traffic insights available to support advanced threat detection.
The Enea Qosmos ixEngine produces the most exhaustive cryptographic-relevant data of any DPI tool. This includes the recognition of PQ-vulnerable encryption protocols and the production of metadata revealing how various users, flows, devices, locations, applications, services, traffic categories, and files are interacting with these protocols.
For instance, Enea Qosmos ixEngine identifies PQ-vulnerable protocols like IPSEC, ISAKMP, OCSP, SSH, SSL, and TOR, and generates extensive metadata for each. For example, for TSL/SSL, Qosmos ixEngine produces well over 100 types of metadata providing key insights into cryptographic elements like public and private keys, cipher suites, handshakes, signatures, client and server fingerprints, certificate authorities, and processing anomalies.
Qosmos ixEngine also produces explicit security metadata for TLS/SSL, like a probability indicator that the domain name mentioned in the Client Hello message has been randomly generated, or a score indicating the probability of a Man-In-The-Middle interception between a client initiating the session and a Man-In-The-Middle box intercepting the SSL/TLS sessions on top of TCP streams.
Enea Qosmos ixEngine can also produce extensive cryptographic-related metadata for traffic which may or may not be encrypted, like Remote Desktop Protocol (Windows Terminal Server), for which Qosmos ixEngine produces more than 50+ types of metadata including – if the connection is encrypted (and one would certainly hope it is!) – specific cryptographic details like the encryption level and method used, client cryptographic configurations, the algorithms used by certificate keys, and encryption methods supported by the client.
This type of data as well of the thousands of other metrics Qosmos ixEngine generates are very well-suited for use in advanced analytics designed to detect subtle patterns and anomalies in cryptographic processes that traditional methods would miss. In fact, though the usage extends far beyond just PQC migration, it is the depth, breadth, accuracy and relevance of Qosmos ixEngine data that makes it the DPI of choice for the EDR, NDR and XDR vendors, who are among those extending their algorithms to detect threats and anomalies related to the transition to a post-quantum world. And to ensure maximum technical and functional performance for their threat detection solutions, most of those vendors are deploying the Qosmos Threat Detection SDK along with Qosmos ixEngine.
Learn More?
To learn more about integrating Enea technology in your PQC migration project, or in broader PQ security initiatives, contact us to arrange an e-meeting.
For a closer look at the threat quantum computing poses to contemporary cryptography, why PQC migration should be begin now, and how to get started see part 1 of this blog.
Endnotes
- Geremew, Amare & Mohammad, Atif. (2024). Preparing Critical Infrastructure for Post-Quantum Cryptography: Strategies for Transitioning Ahead of Cryptanalytically Relevant Quantum Computing. International Journal on Engineering, Science and Technology. 6. 338-365. 10.46328/ijonest.240.