Get Ready for Post-Quantum Cryptography with Enea Qosmos Technology, Part 1 of 2
The Quantum Threat and the Need to Act Now
There are two major technology evolutions reshaping the future of cybersecurity today: AI and quantum computing. Of the two, AI captures the lion’s share of attention as it is rewriting the rules of cybersecurity in real time, while quantum computing is still in an R&D phase – like an ocean swell forming at sea versus the AI tsunami crashing our shores. Organizations therefore feel time is on their side in preparing for the impacts of quantum computing on their networks.
In reality, however, the right time to begin preparing for a quantum world is…yesterday. While quantum computing, like AI, carries both benefits and risks for cybersecurity, the gravity of the risk – and the complexity of mitigating it – makes preparing now an urgent matter. For the day is coming when we will be confronted with a class of quantum computers that can run the powerful Shor’s & Grover’s algorithms, which can respectively be used to break or weaken the cryptographic algorithms at the heart of our global public key infrastructure.
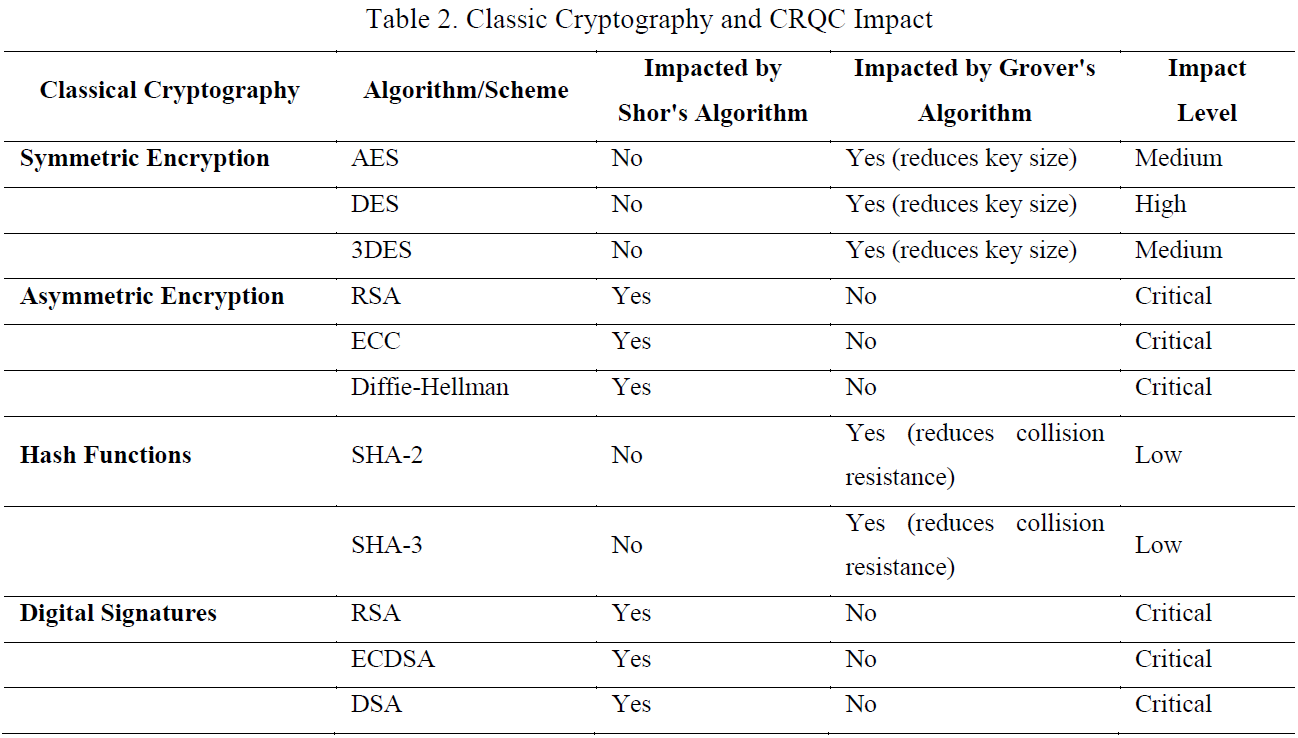
Table by Geremew & Mohammad (2024) summarizing the anticipated impact of Shor’s & Grover’s algorithms on the key components of contemporary cryptography.1
Such a development would expose all our encrypted data to the risk of exfiltration or tampering, including all the encrypted data compromised by prior ‘harvest now, decrypt later’ attacks executed in anticipation of quantum-powered decryption.3 At the same time, migrating to quantum-safe (or ‘post-quantum’) cryptography is a complex and lengthy process due to how deeply and widely embedded cryptographic assets and systems are in modern networks.
Fortunately, whether you are a software vendor, a managed security services provider, or an IT team leader, if you are (or plan) to support PQC migration, there are technologies that can help make your solution faster, easier and more successful. Specifically, deep packet inspection (DPI) software, that carries out detailed network traffic analysis, can accelerate PQC migration by bringing critical visibility to the initial discovery phase, thereby making the subsequent planning and execution phases more efficient and effective. New threat detection software that integrates tightly with the DPI functions can strengthen post-migration monitoring and remediation as standards and networks evolve (i.e., it enables ongoing ‘crypto-agility’).
To better understand these benefits, let’s begin with a closer look at the nature and progress of quantum computing, followed by an overview of primary PQC processes. Then in the second installment of the blog, we’ll take a close look at the role of DPI and integrated threat detection capabilities within those processes.
The Power of Quantum Computing
AI-generated image of a Quantum computer
Quantum computers are radically different from conventional computers. Their design is based on the complex (and still mysterious) physics of the tiniest building blocks of the universe, like electrons and photons. Accordingly, they operate via complex superimposed and entwined ‘qubits’ (quantum bits) instead of traditional computers’ simple 1/0 bits, which represent the binary on/off states of electrical systems.
This radically different architecture makes quantum computers astonishingly good at complex computations. For example, Google’s latest generation 105-qubit quantum computer, Willow, recently performed a computation in under 5 minutes that would take one of the world’s fastest supercomputers 10 septillion years to complete: that’s 10,000,000,000,000,000,000,000,000 years (a time frame that dwarfs the estimated age of the universe).2
Forecasts for the Arrival of “Q-Day”
As startling as this achievement is, Google says it would take a far more powerful quantum computer – one with around 4 million qubits – to break the common cryptographic algorithm RSA (Rivest-Shamir-Adleman).3 Google estimates they are at least 10 years from developing such a quantum computer, a milestone often referred to as Q-Day. But Google isn’t the only player on the field, and sometimes (as AI shows) exponential leaps can happen unexpectedly.
Perhaps such reasons factor into the estimation by the Cloud Security Alliance (CSA) that we are only 5 years away from a quantum computer that is scalable and stable enough to break RSA and other widely used cryptographic schemes (like Diffie-Hellman and ECDHE).4 This aligns with the timeline outlined by the U.S. National Institute of Standards and Technology (NIST), which has set an official deadline for transitioning away from quantum-vulnerable encryption algorithms (specifically RSA, ECDSA, EdDSA, DH & ECDH) by 2030, and completely disallowing them by 2035.5

To encourage action now, the Cloud Security Alliance maintains a “Y2Q” (Years-to-Quantum) countdown clock on its Quantum-Safe Security Research Topic web page.6
The Need to Begin the Migration to PQC Now
While the five-year worst-case scenario sounds fairly generous for many types of IT projects, past encryption transitions have proven to be lengthy (e.g., the decade-plus shift from SHA-1 to SHA-2 cryptographic hash functions), and it is in any case uncomfortably short for many organizations, such as those in critical infrastructure industries, who both have complex networks and can’t afford to be caught unprepared.
And for everyone, it is a fact that migrating to post-quantum cryptography touches every facet of a network, everywhere – from networking and transport infrastructure to security appliances and web services, from data centers and cloud platforms to APIs, from enterprise and OT applications to host and endpoint devices, from source code to binary files, and so on.
This is why NIST and other standards bodies suggest taking action now. And other regulatory authorities worldwide either have or will follow NIST’s footsteps in establishing deadlines for government agencies and critical industries to begin transitioning to a PQC environment. Thankfully, many have already issued PQC migration guidelines and recommendations, including the European Telecommunications Standards Institute (ETSI), France’s Agence nationale de la sécurité des systèmes d’information (ANSSI), Germany’s Bundesamt für Sicherheit in der Informationstechnik (BTI), and the UK’s National Cyber Security Centre (NCSC), along with industry organizations like CSA.7 In addition, as of March 11, 2025, NIST has published five PQC algorithms which organizations can use to replace vulnerable algorithms, three of which are formally approved Federal Information Processing Standards (FIPS).8
Key PQC Migration Steps
While migration guidelines vary in the names and numbers of steps recommended, they generally encompass four basic clusters of activity, namely discovery, planning, execution, and monitoring.
-
Discovery
The discovery phase begins with establishing roles and responsibilities, followed by creation of a complete inventory of all vulnerable cryptographic resources (algorithms, algorithmic libraries and certificates) that need to be upgraded or replaced. But you can’t update or replace what you can’t see, and every organization has both known and unknown visibility gaps in their networks. So filling these network visibility gaps is a mission-critical first step in inventory development. Once the cryptographic inventory has been completed, the planning phase of PQC migration can begin.
-
Planning
The goal of this phase is to establish priorities and create an action plan and/or roadmap for the migration. It should include prioritization of actions based on the vulnerability level of each cryptographic resource (e.g., asymmetric vs symmetric algorithms), the sensitivity of the data involved, dependencies between resources, and the level of difficulty in upgrading or replacing vulnerable algorithms. Roles and responsibilities, budgetary needs and business process updates should naturally all be included as well.
-
Execution
In this phase the roadmap or action plan is executed, accompanied by regular testing and validation. There will also be adaptations in some cases to accommodate resource constraints and performance issues associated with PQC (e.g., PQC keys are larger than current keys, and handshakes can be longer and more complex). All actions taken should be documented with any issues, exceptions, changes, etc. recorded, and regular migration reports should be prepared as PQC is a long process.
-
Monitoring
Once the initial plan is executed, there needs to be continuous monitoring to ensure one’s systems remain resilient in the face of inevitable network evolutions, to adapt to changes in post-quantum standards and PQC algorithms, and to respond to any new quantum risks. In other words, the goal of success here is to achieve enduring “crypto-agility”.
Know more?
To understand how Enea DPI and threat detection software components in particular help with this migration process, see Part 2 of this blog.
Endnotes
- Geremew, Amare & Mohammad, Atif. (2024). Preparing Critical Infrastructure for Post-Quantum Cryptography: Strategies for Transitioning Ahead of Cryptanalytically Relevant Quantum Computing. International Journal on Engineering, Science and Technology. 6. 338-365. 10.46328/ijonest.240.
- https://blog.google/technology/research/google-willow-quantum-chip/
- https://www.theverge.com/2024/12/12/24319879/google-willow-cant-break-rsa-cryptography
- https://cloudsecurityalliance.org/research/topics/quantum-safe-security
- https://csrc.nist.gov/pubs/ir/8547/ipd
- https://cloudsecurityalliance.org/research/topics/quantum-safe-security
- ETSI: https://www.etsi.org/deliver/etsi_tr/104000_104099/104016/01.01.01_60/tr_104016v010101p.pdf
ANSSI: https://cyber.gouv.fr/en/publications/follow-position-paper-post-quantum-cryptography
BTI: https://www.bsi.bund.de/EN/Themen/Unternehmen-und-Organisationen/Informationen-und-Empfehlungen/Quantentechnologien-und-Post-Quanten-Kryptografie/Post-Quanten-Kryptografie/post-quanten-kryptografie_node.html
UK NCSC: https://www.ncsc.gov.uk/news/pqc-migration-roadmap-unveiled - https://www.nist.gov/news-events/news/2025/03/nist-selects-hqc-fifth-algorithm-post-quantum-encryption