Effective SSE = ZTNA + CASB + SWG + NG DPI
What is SSE and how does Next-Gen DPI make it more effective?
SD-WAN
SD-WAN was a starting point for cloud-based networking and security. It stands for Software Defined Wide Area Networking and is since 2015 gradually replacing Virtual Private Networks (VPNs) based on Multiprotocol Label Switching (MPLS) for enterprise connectivity. A typical SD-WAN solution includes traffic optimization, security and reporting functions.
SASE = SD-WAN + ZTNA + CASB + SWG
In 2019, Gartner analysts coined the term SASE, or Secure Access Service Edge, to describe the cloud-centric security capabilities that facilitates safe access to websites, software-as-a-service (SaaS) applications and private applications.
SASE (pronounced sassy) is the combination of SD-WAN and 3 key cloud security functions:
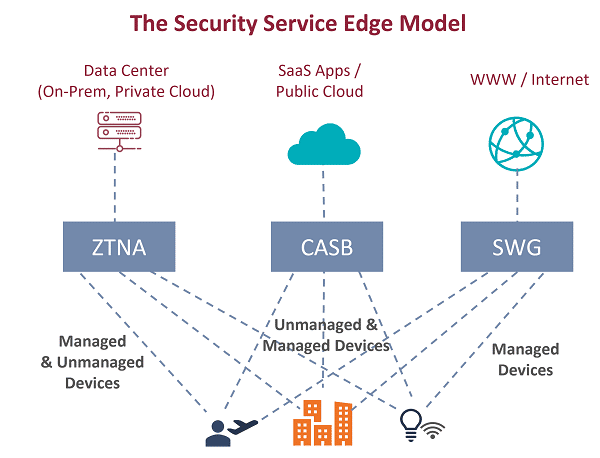
- Zero Trust Network Access (ZTNA) to access remote private apps
- Cloud Access Security Broker (CASB) to access SaaS and cloud apps
- Secure Web Gateway (SWG) to access to the Internet
Note that some SASE vendors also include in Data Loss Prevent (DLP), Next Generation Cloud Firewall (NG CFW), Web Application Firewall (WAF), and/or Intrusion Detection/Prevention (IDS/IPS).
SSE = SASE – SD-WAN = ZTNA + CASB + SWG
In many cases, SD-WAN connectivity, the “A” (Access) in SASE, is not needed, which gives us “Secure Service Edge” or SSE, as a combination of ZTNA, CASB and SWG.
NG DPI = Real-time traffic visibility
Whatever the acronym, cloud-based security solutions all need detailed, real-time traffic visibility to classify traffic for network operations, policy control, and detection of malicious activity.
This visibility is provided by embedded Next Gen Deep Packet Inspection (NG DPI). NG DPI goes beyond traditional DPI, adding specifically developed techniques to meet three important challenges:
- The rise of encrypted traffic, which impacts the essential visibility required to properly manage and secure networks,
- The emergence of advanced, complex cyberattacks perpetrated by sophisticated criminal actors and nation-states, and
- The shift to cloud-based solutions, with significantly higher performance and scalability requirements.
NG DPI meets these challenges with these distinguishing capabilities:
- Encrypted Traffic Classification (ETC)
- Detection of anomalous & evasive traffic
- Advanced first packet processing
- Extended protocol & application signatures
- Cloud-scale performance
NG DPI is particularly important for effective SSE. To find out more about embedding NG DPI into SSE solutions, I encourage you to download our technical white paper: How SSE Leaders Use Next Generation DPI for Market Success.





